1. Update your technology
Download the latest firmware for your micro:bits and install the required Python module on your TI graphing calculators.
Updates for the TI-84 Plus series Updates for the TI-Nspire™ series
Download hands-on, interactive cybersecurity activities for students that promote teamwork


Download the latest firmware for your micro:bits and install the required Python module on your TI graphing calculators.
Updates for the TI-84 Plus series Updates for the TI-Nspire™ series

After downloading all the activities, transfer the files to your TI graphing calculators using your software or the web-based app.
Transfer files for TI-84 Plus series Transfer files for TI-Nspire™ series

Provide every member of a group (typically three students per group) a micro:bit and a graphing calculator.
Select one of the cybersecurity activities from the calculator’s menu options and follow the step-by-step instructions.
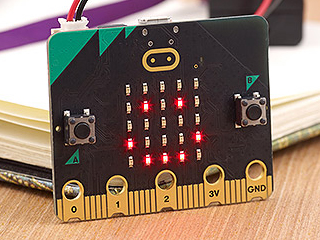
The micro:bit is a multifunctional microcontroller board that creates a fun, interactive learning environment for students to learn the basics of physical computing.
These free cybersecurity activities are ordered in a series of learning sequences, so students can gradually build on their understanding concept by concept.
Download all the activities:

Activity 1 introduces students to “cleartext” messaging. Students will send messages between two micro:bit radios on one of 83 radio channels using plaintext characters, referred to as cleartext. The “student hacker” will attempt to eavesdrop on the conversation by listening in on the same channel.

Inspired by Hedy Lamarr’s revolutionary work, this activity builds on the concepts learned in Activity 1 and introduces students to frequency hopping. Students will learn the method of hiding radio messages by transmitting bits and pieces over several radio channels until an entire message has been sent, making it very difficult for an eavesdropper to intercept them.

Building on the concepts learned in Activity 2, this activity introduces students to Caesar ciphers. Students will experiment with encoding messages by using a Caesar shift, which is used to switch up the order of letters in the alphabet to transform plaintext into a ciphertext.

Building on the concepts learned in Activity 3, students will learn about obfuscating passwords through a method known as “hashing.” This security function shows students how a plaintext password can be scrambled and encrypted by a hashing function, such as SHA-256, in such a way that makes it unreadable to hackers.

Building on the concepts learned in Activity 4, it’s up to the student hacker to turn the tables by working out the method for hacking SHA-256 password encryption.
The
student hacker must search a rainbow table, which is comprised of precomputed hashes from known and frequently used passwords, to decrypt the hashed password
they’ve stolen.

Building on the concepts learned in Activity 5, the student hacker will now attempt a brute force attack to decrypt the hashed password. The students will observe the key differences between this and the rainbow table method.

This bonus activity challenges students to put all the concepts they’ve learned together in order to successfully pick a micro:bit lock. Will your students be able to discover what’s locked away inside the old treasure chest?

Challenge students to strengthen their problem-solving skills by identifying patterns, solving puzzling problems and unraveling clues to triangulate the rich point on a treasure map.